

Product Features: security
Secure by design
When incorporating multimodal AI into your organization’s processes, it is imperative to know where your data is managed and stored. With Cordoniq, you have the peace of mind knowing that all your real-time AI data intelligence–including video, audio, text, documents, images and collaboration material–is completely behind your firewall, on-premises or in a private or public cloud of your choosing.
Cordoniq is built for all types of organizations, including those that require the highest level of data protection, such as governmental agencies, the Department of Defense (DoD) and R&D teams.
At Cordoniq, we take the secure-by-design approach to software development and vision AI integration. We build security directly into our platform and integration processes. Cordoniq also offers a fully containerized and isolated model, for those seeking the highest data security.
Learn how secure-by-design software can improve security
Mitigate the risks
While many products that integrate AI claim they’re secure, all they’re really doing is basic encryption of your business communications, or offering vague privacy policies for your data. This means your shared materials and information are prone to cyber hacking or by training use of their AI models.
Cordoniq is designed to mitigate the risk of data breaches, brute force attacks, cyber hacking, intrusion and other cyber attacks. That’s why the U.S. Department of Defense chooses Cordoniq to meet its stringent requirements for military-grade security for virtual collaboration.
Learn how Cordoniq scored a hat-trick at 2024 Cybersecurity Excellence Awards

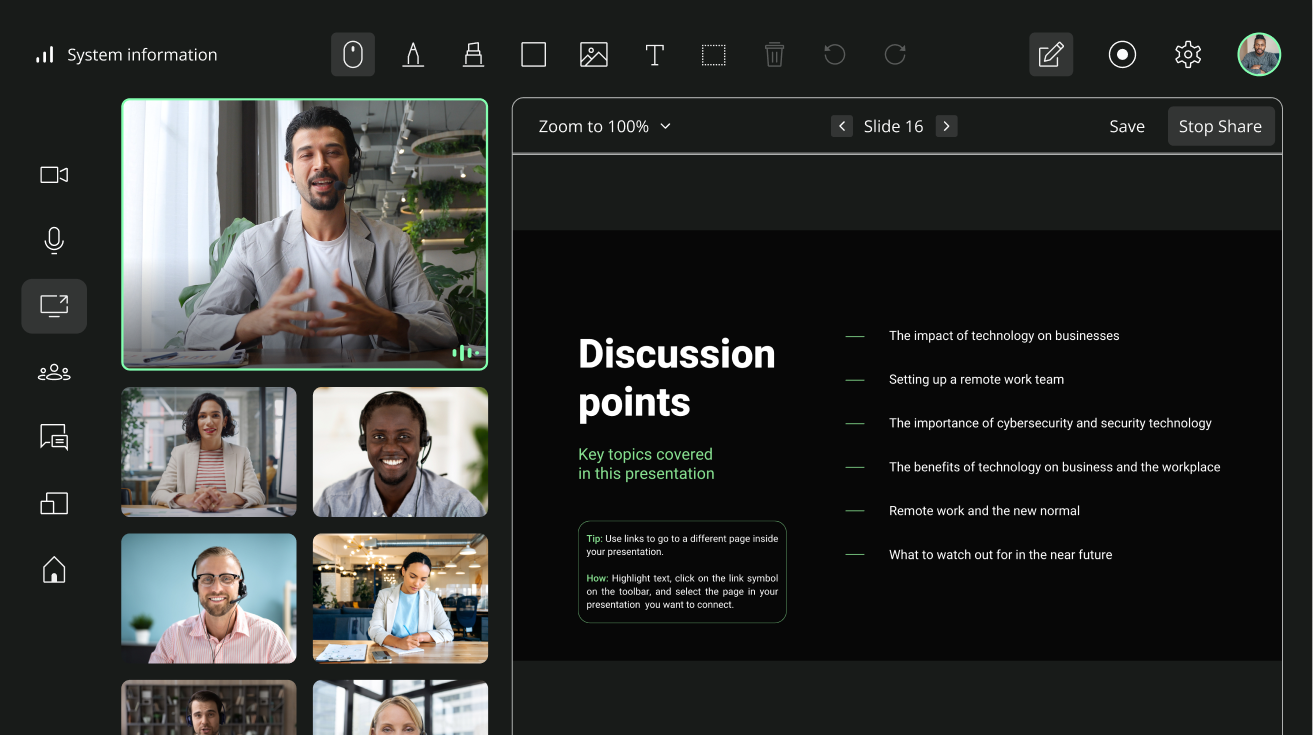
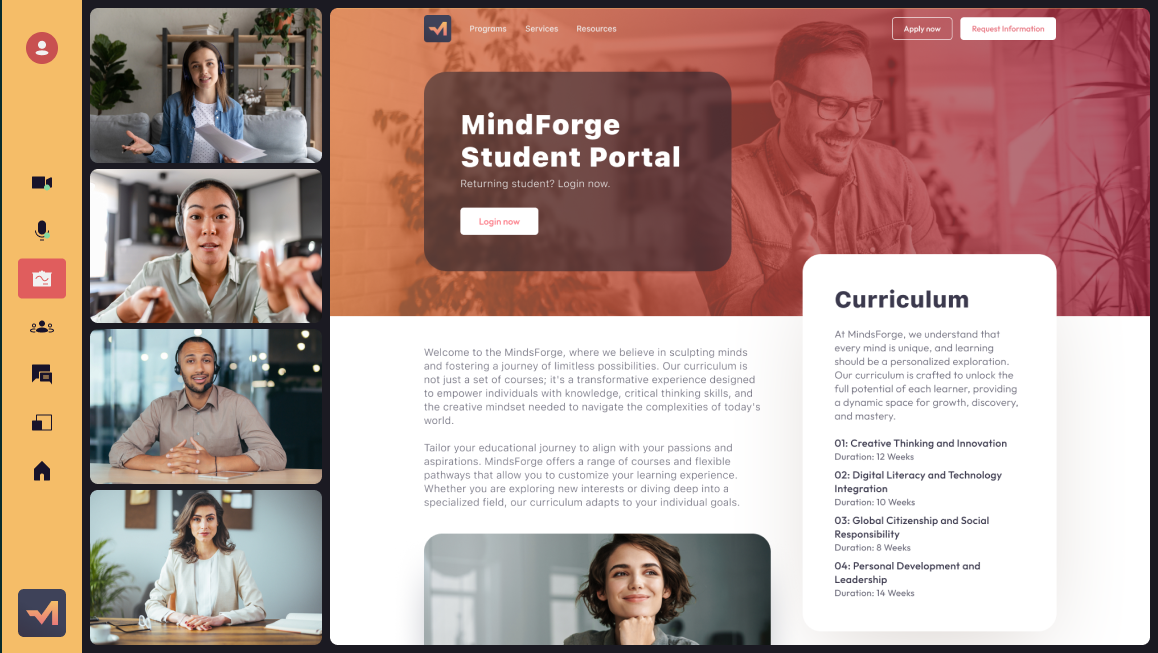
Secure & control your user experience
We are your implementation partner to secure your AI business intelligence. We will build directly into your tech stack for smooth, real-time data functionality at scale.
Capture all of your global meeting intelligence data during live virtual meetings within your organization, and easily access any data immediately, from any meeting, anywhere.
You have complete control of all aspects of your business processes with AI-integrated data, including live and interactive user experiences. You control where multimodal AI data and recordings, videos, documents, files and audio are accessed, managed and stored.

Integration control
Multimodal AI
We securely integrate real-time transcoding AI in the cloud or on-premises deployment, with these AI models: Alibaba’s Qwen, Google Gemini and OpenAI ChatGPT.
Our framework excels at capturing and processing real-time data from a wide range of sources:
- Multimedia: Text, video, audio, speech, images
- Sensory: Tactile, sensor data
- Digital: Text, whiteboards, documents, webpages, live annotations, chats
Cordoniq scales effortlessly and integrates securely with your existing AI models, enabling bi-directional communication and delivering actionable and engaging real-time experiences.
APIs
With Cordoniq, you can also leverage APIs to control your organization’s data and proprietary information privacy. Every aspect of the experience–both on the front end and back end–can be controlled and available via API. You have control over the entire app experience (Windows, macOS, iOS and Android).






For administrators & developers
For IT administrators and developers, we provide the AI service modules that connect the AI multimodal inputs from various sources to the AI model–in real-time. Our AI service modules are elastic, secure and highly scalable.
As IT administrators, you can choose your cipher strength and PKI key depth rules. Your company can provide its security certificates and use its internet domain names, which are easily implemented using our robust Cordoniq Developer Portal or through our development services.